IAM SAR-ry: Deep Dive and Nuances of AWS's Programmatic IAM Action List and Service Authorization References (SAR)
A few weeks ago, we recently gave a talk at fwd:cloudsec 2025, a non-profit conference on cloud security for practitioners, on the Duplictious Nature of AWS IAM. While preparing our slides for the talk, we uncovered a recent update by AWS on their AWS IAM listings: an update to their programmatic IAM action listing on action classification.
We continued that research on both the programmatic IAM action listing as well as the service authorization reference (SAR) pages. Our findings include:
- Change in AWS's IAM Action Classification.
- How integrating the programmatic IAM action listing into your IAM workflows may lead to some inconsistencies.
- Differences between the programmatic action listing and the SAR pages.
We published insights and refernece information at our GitHub: https://github.com/FogSecurity/aws-iam/tree/main/service_reference.
Reach out to us at info@fogsecurity.io with any feedback or if you want to continue the conversation! All statistics below are as of July 2025 and are subject to change. See our Github for the most up to date information.
Overview
In late 2024, AWS released programmatic service reference information in json format. This helps with IAM policy workflows. Previously, open source libraries and other resources had to rely on Service Authorization Reference (SAR) pages. Tooling that needed to programmatically retrieve information about IAM actions previously had to scrape SAR web pages or other indirect sources. This tooling includes Fog Security's (our own) tooling and other tools such as permissions.cloud.
For an overview of the programmatic service reference release, see Rowan Udell's post here.
AWS Timeline on Programmatic Service Reference Information
- Late 2024: AWS releases Programmatic Service Reference Information
- March 2025: AWS adds resources and condition keys to service reference information.
- June 2025: AWS adds action properties (such as write or list) to service reference information.
Observations
These observations are all from July 10th, 2025 and are subject to change. We will periodically update our GitHub to reflect updated information across both the programmatic service reference and the service authorization reference pages.
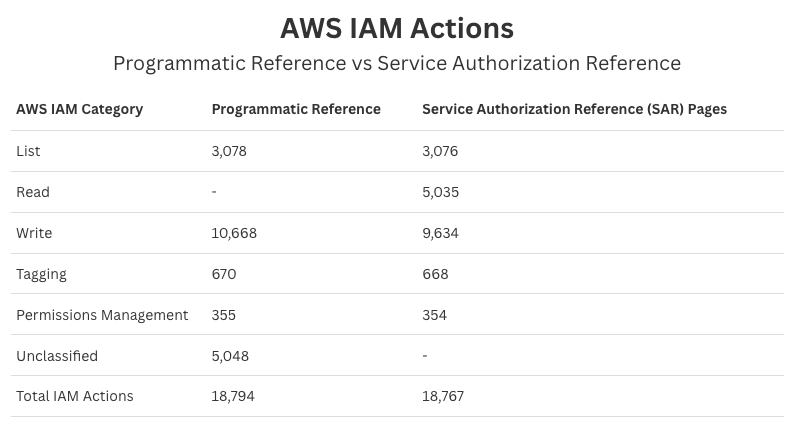
Summary Statistics and Comparison
With the new programmatic service reference, actions now can have multiple classifications. Overall changes include the addition of "write" to actions that are permissions management and tagging. Thus, we can use the following graphs to represent the difference in permissions.
%20copy.png)
More details of why the summary statistics look different will be found below.
Inconsistency Across Programmatic and Service Authorization Reference Pages
- 118 Duplicate Actions in the Service Authorization Reference Pages. The duplicates are not present in the programmatic reference. These cover services with multiple versions such as:
- API Gateway v2 and API Gateway (v1)
- Elastic Load Balancing v2 and Elastic Load Balancing (v1)
- IoT Greengrass v2 and IoT Greengrass (v1)
- Kinesis Analytics v2 and Kinesis Analytics (v1)
- Lex v2 and Lex (v1)
- Amazon Pinpoint Email Service and Simple Email Service (SES)
- Simple Email Service v2 and Simple Email Service (v1)
Github: https://github.com/FogSecurity/aws-iam/blob/main/service_reference/sar_duplicates.json
- 27 Actions in Programmatic Reference, but not in SAR. These are mostly tied to the IOT 1 Click service and 1 network firewall permission.
Github: https://github.com/FogSecurity/aws-iam/blob/main/service_reference/actions_in_prog_not_sar.json
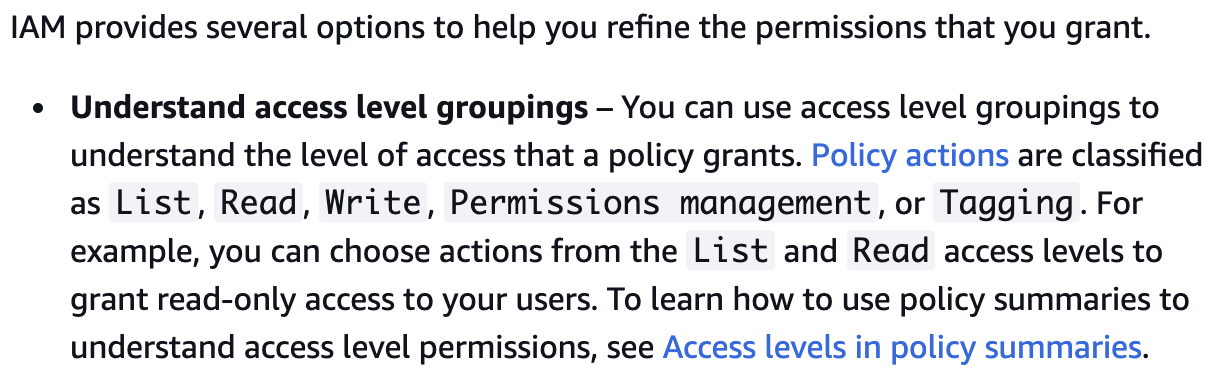
Access Levels: N > 1
Previously, actions were classified as one specific category: List, Read, Write, Tagging, and Permissions Management. These categories are used to classify access levels of policies as well as access levels of permission sets. For example, there's a difference between list and read where read access is associated more with data read when list is associated more with resource listing and metadata.
From the previous categories, there are 10 different combinations of N = 2 categories, but we will only see 2 main classifications:
- Write and Tag
- Permissions Management and Write
This helps clarify some confusing permissions. As we covered in our fwd:cloudsec talk, example permissions are both sqs:SetQueueAttributes and sqs:AddPermission which can both modify the SQS Queue Policy that can grant access to the queue.
sqs:AddPermissionfrom the SAR is classified as Permissions Management.sqs:SetQueueAttributesis classified as Write.
Now, with the programmatic action reference, both actions are classified as both Permissions Management and Write.
We didn't see and don't expect to see Tagging and List, List and Write, or List and Permissions Management. However, we will continue running automation to check.
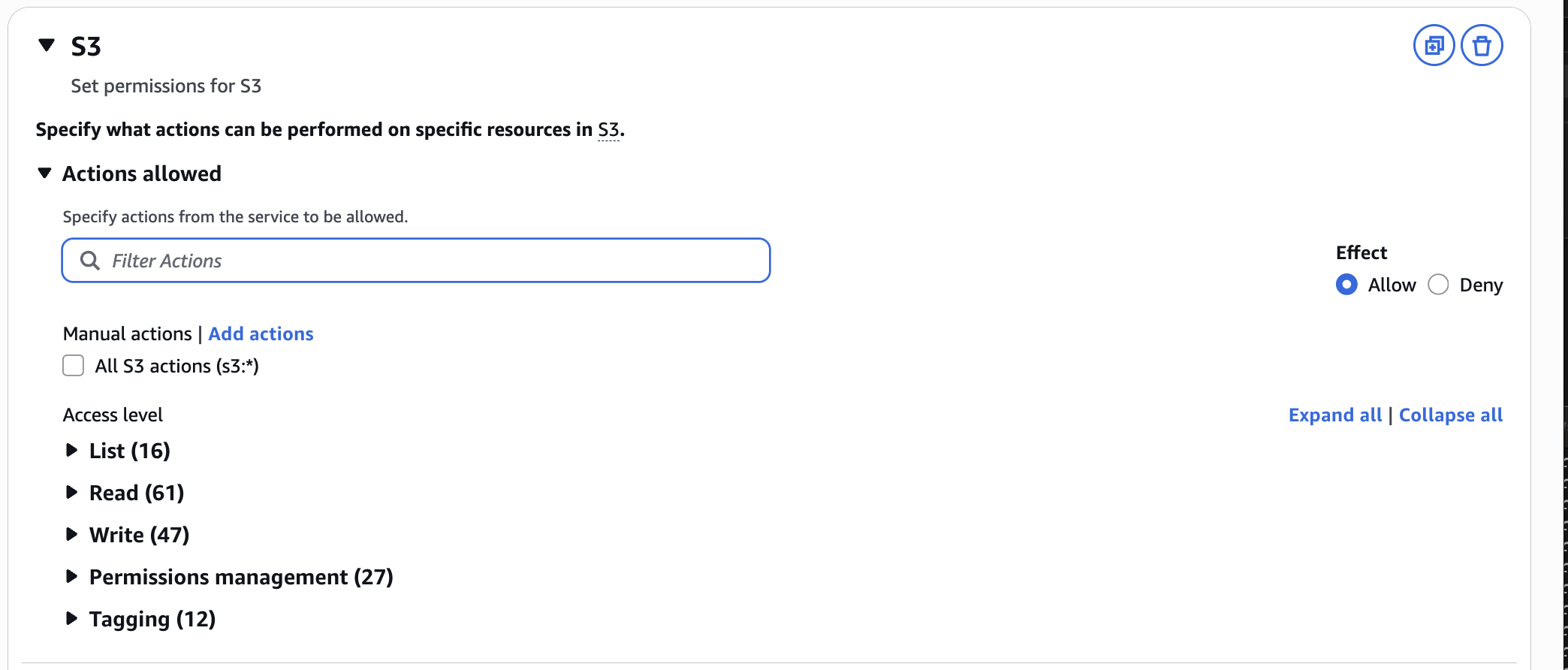
With the new programmatic action listing, actions may have more than 1 access level (as denoted by AWS's property annotations).
The highlights of this change are:
- 355 actions classified as both Permissions Management and Write.
- 670 actions classified as both Write and TaggingOnly.
- All Permissions Management and TaggingOnly permissions are classified as Write actions.
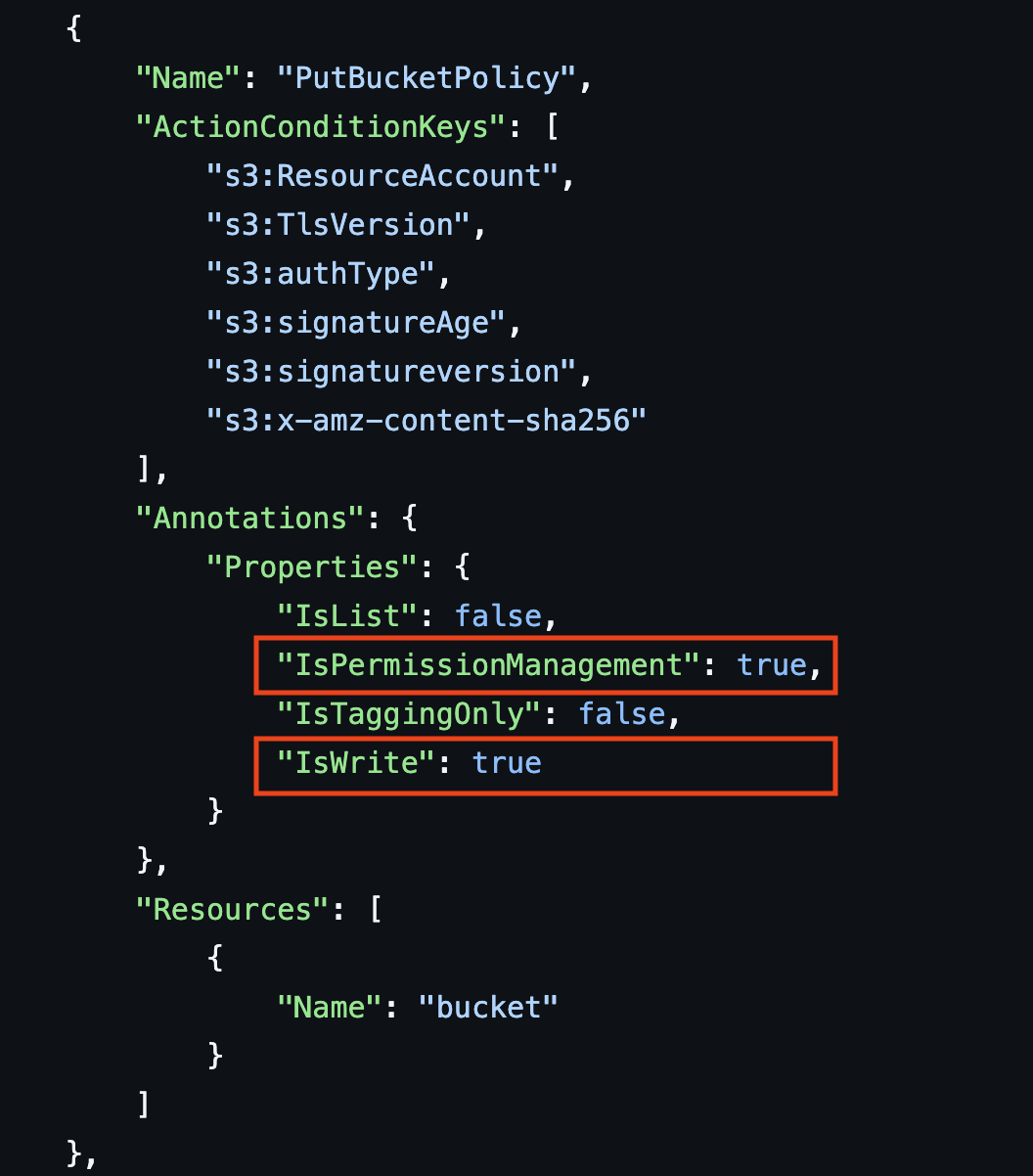
From looking at our Service Authorization Reference pages and, there are 2 main changes:
- Most Permissions Management Actions (355) from SAR are classified as Permissions Management and Write.
- Most Tagging Actions (670 actions, there are 12 actions that have been moved) are now classified as TaggingOnly and Write.
GitHub for Permissions Management and Write: https://github.com/FogSecurity/aws-iam/blob/main/service_reference/perm_and_write.json
GitHub for Tagging and Write: https://github.com/FogSecurity/aws-iam/blob/main/service_reference/write_and_tag.json
Missing Read in Programmatic List
The programmatic list has 4 categories:
- IsList
- IsPermissionsManagement
- IsTaggingOnly
- IsWrite
There is no read annotation property in AWS's new programmatic reference. We can surmise and assume that an IAM action not classified as List, Write, TaggingOnly, or Permissions Management will be a read action - but this is not clear.
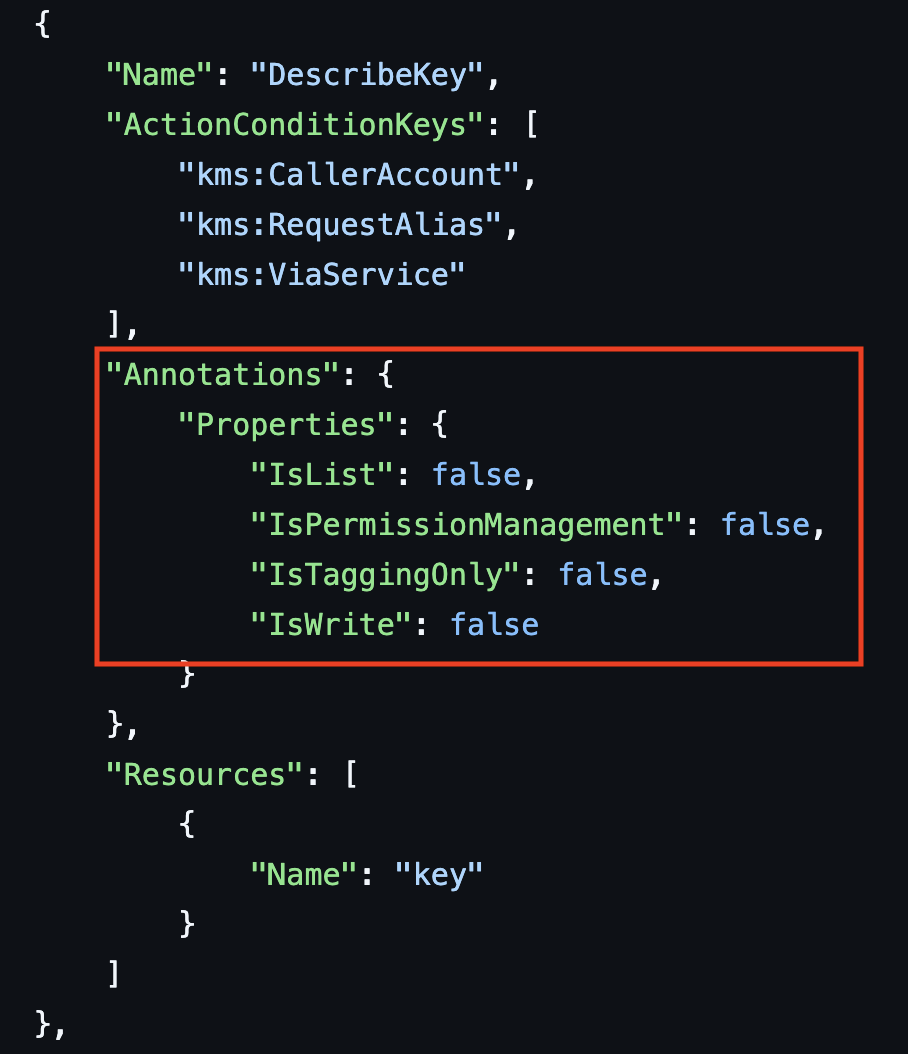
Inconsistent Action Classifications
In our repository, we've also categorized actions that are classified differently from both the programmatic reference and the service reference pages.
- 1,023 IAM Actions that have additional categories.
For these actions, we cross referenced all permissions in both the Service Authorization Reference pages and in the programmatic reference and compared Access Levels in the SAR pages with the property annotations in the programmatic reference to see waht changed.
GitHub: https://github.com/FogSecurity/aws-iam/blob/main/service_reference/actions_add_cat.json
Tagging Only
For Service Authorization Reference pages, the Tagging Access Level was simply defined as Tagging.
In the programmatic action listing, tagging is identified by "IsTaggingOnly" and defined as "Provides permissions only for modifying tags".
While this is a minor change, there are some changes from the Service Authorization Reference with the addition of "only" and defining it as "only for modifying tags."
We see the following clarifications and differentiations:
- Actions classified as
TaggingOnlywill only be able to modify tags and no other metadata or properties. - Actions that can modify other metadata or properties will not be classified as
TaggingOnly - Only actions that can modify tags (not only read) tags will be classified as
TaggingOnly. - Actions that can only read or view tags will not be classified as
TaggingOnly
We see a difference of 12 IAM Actions with 670 TaggingOnly actions and 682 SAR actions classified as Tag.
Conclusion
We like the release of AWS's programmatic action list and their continued updates to the listing. This helps reduce the reliance on web scraping the service authorization pages in AWS. We recommend to use caution when changing over to AWS's programmatic action list as there are differences between the programmatic lists and SAR pages (and tooling that references the SAR pages).
We will keep our GitHub periodically updated with our observations above and the service reference pages so point-in-time references can be made to view changes and differences between both the programmatic list and SAR pages to help with your AWS IAM workflows.
Reach out to us at info@fogsecurity.io with any feedback or if you want to continue the conversation!
Resources and References
AWS Service Reference Documentation