Mistrusted Advisor: Evading Detection with Public S3 Buckets and Potential Data Exfiltration in AWS
Executive Summary
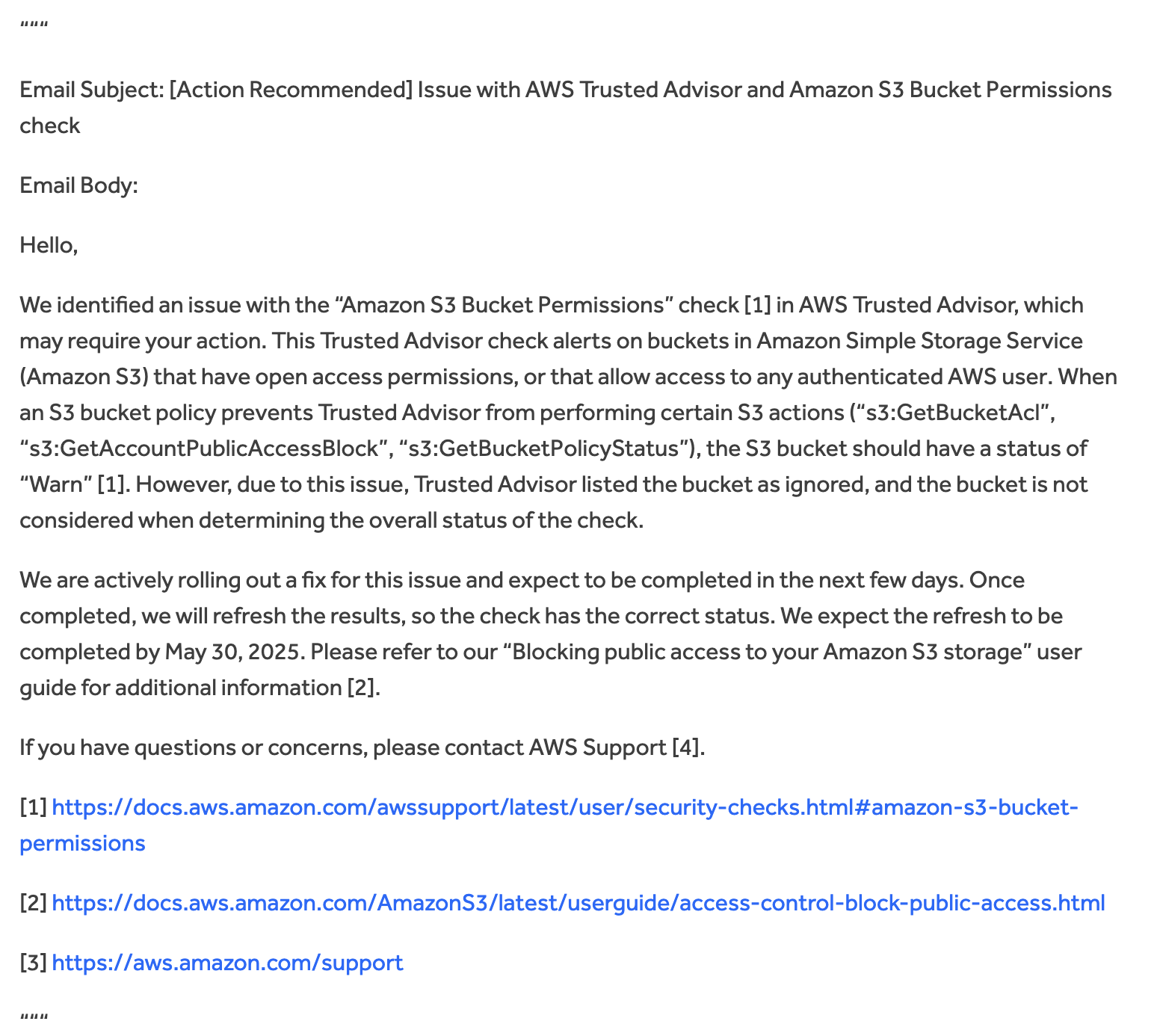
In May 2025, we uncovered multiple undocumented techniques to evade detection by bypassing AWS Trusted Advisor’s S3 Security Checks. Leveraging these methods, we were able to bypass detection by Trusted Advisor’s S3 security scans and configure buckets with public and anonymous permissions via bucket policies and ACLs which permit data access open to the world and potential data exfiltration - all without triggering a single alert.
Under these conditions, Trusted Advisor incorrectly reported these public S3 buckets as secure, potentially leaving sensitive data exposed to data exfiltration and data breaches. Trusted Advisor’s S3 Bucket Permission check is one of the only complimentary S3 security detective controls offered natively by AWS without enablement. All AWS customers get Trusted Advisor’s S3 security check for free (customers with certain paid support plans receive API access and auto-refreshed checks).
This post will cover our security findings with Trusted Advisor including a walkthrough, our recommendations, our partnership with AWS to resolve these issues, and AWS's response. While we appreciate AWS addressing the issue, we found AWS's customer communication lacking and that their communication downplayed the impact and severity of this issue.
We reported this issue to AWS in May 2025. As of late June, 2025 this is no longer an issue.
Timeline
- May 2nd, 2025: Fog Security submitted an initial report to AWS VDP via HackerOne.
- May 12th, 2025: AWS confirmed validation of the initial report and committed to deploying code changes for a fix.
- May 30th, 2025: AWS confirmed implementation and deployment of code fix across all AWS partitions and regions and a refresh for the Trusted Advisor S3 check to ensure all customers now have the correct status displayed.
- June 10th, 2025: AWS confirmed an email communication was sent out to affected customers.
- June 13th, 2025: Fog Security retested and noticed still incorrect results for ACLs. Fog Security notified AWS of the testing results and AWS’s incomplete change.
- June 30th, 2025. AWS deployed an additional fix with no additional customer communication.
- August 15th, 2025. AWS updated their statement based on our feedback.
- August 20th, 2025. Fog Security and AWS coordinated disclosure with Fog Security blog and AWS's public statement.
Finding Overview
We discovered 3 distinct scenarios where Trusted Advisor’s alerting could be bypassed and would not alert on Public Buckets:
- A S3 Bucket Policy that denies
s3:GetBucketPolicyStatus - A S3 Bucket Policy that denies
s3:GetBucketPublicAccessBlock - A S3 Bucket Policy that denies
s3:GetBucketAcl
With these scenarios, a bucket could then be configured for data exfiltration with any of the following granting public access:
- Public ACLs (and Block Public Access disabled)
- Public Bucket Policy (and Block Public Access disabled).
In this case, we found the following:
- Improperly reported status of the Trusted Advisor S3 check where:
- Expected red (action recommended) result improperly reported as green (no problems detected).
- Expected yellow (investigation recommended) result improperly reported as green (no problems detected).
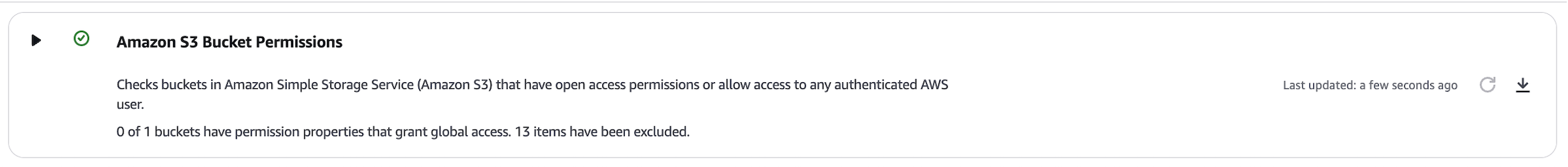
- Improperly reported ACL status:
- “No” for ACL Allows List despite a public ACL that allows listing.
- “No” for ACL Allows Upload/Delete despite a public ACL that allows upload/delete.
- Bucket Policy was not evaluated.
- Bucket categorized as “ignored bucket” but was not evaluated in the overall Trusted Advisor S3 security check.
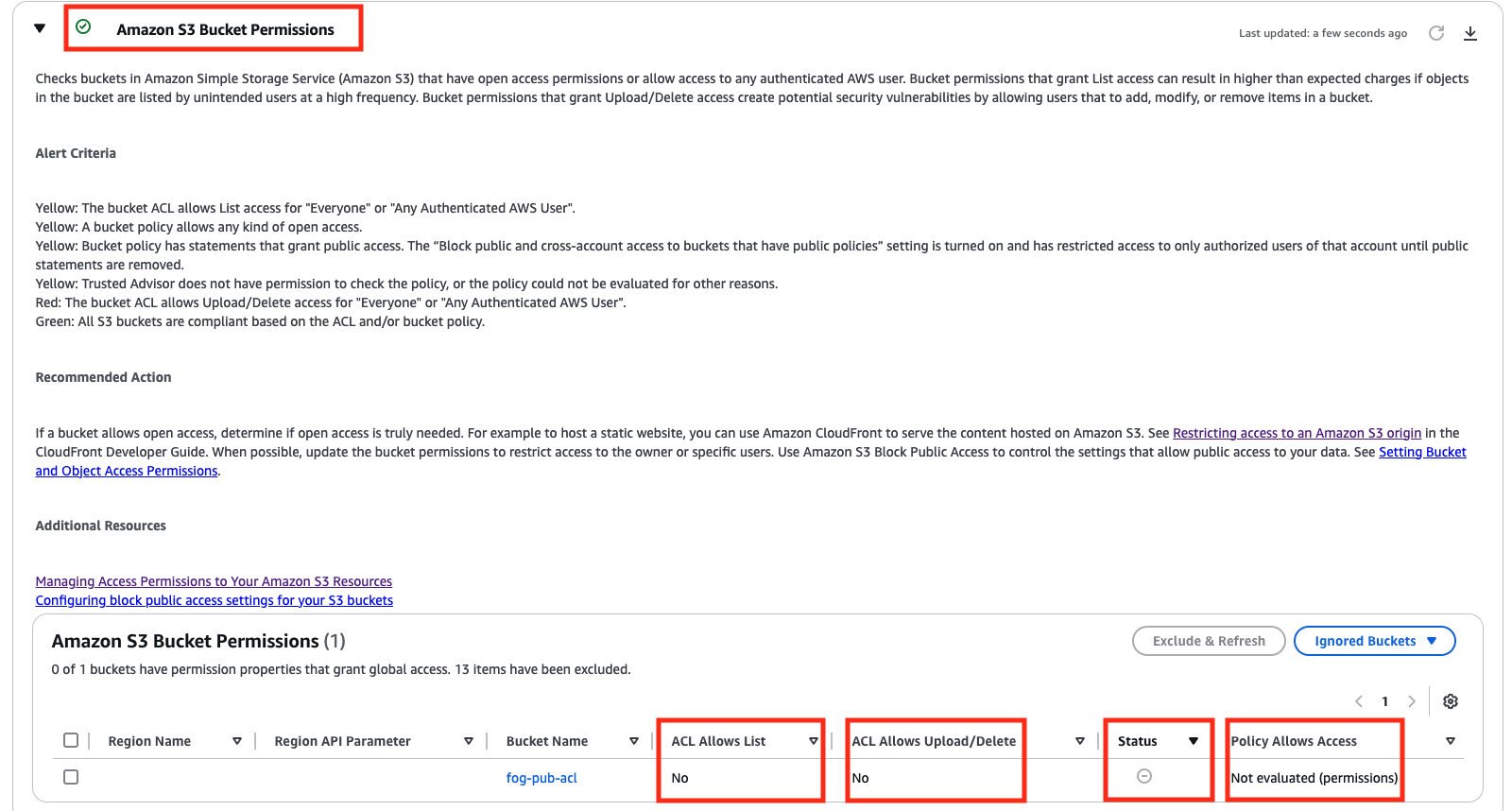
Trusted Advisor surfaces a summary of all the findings and will also improperly summarize this inaccurate reporting as not a finding.
Background and Walkthrough
Trusted Advisor Background
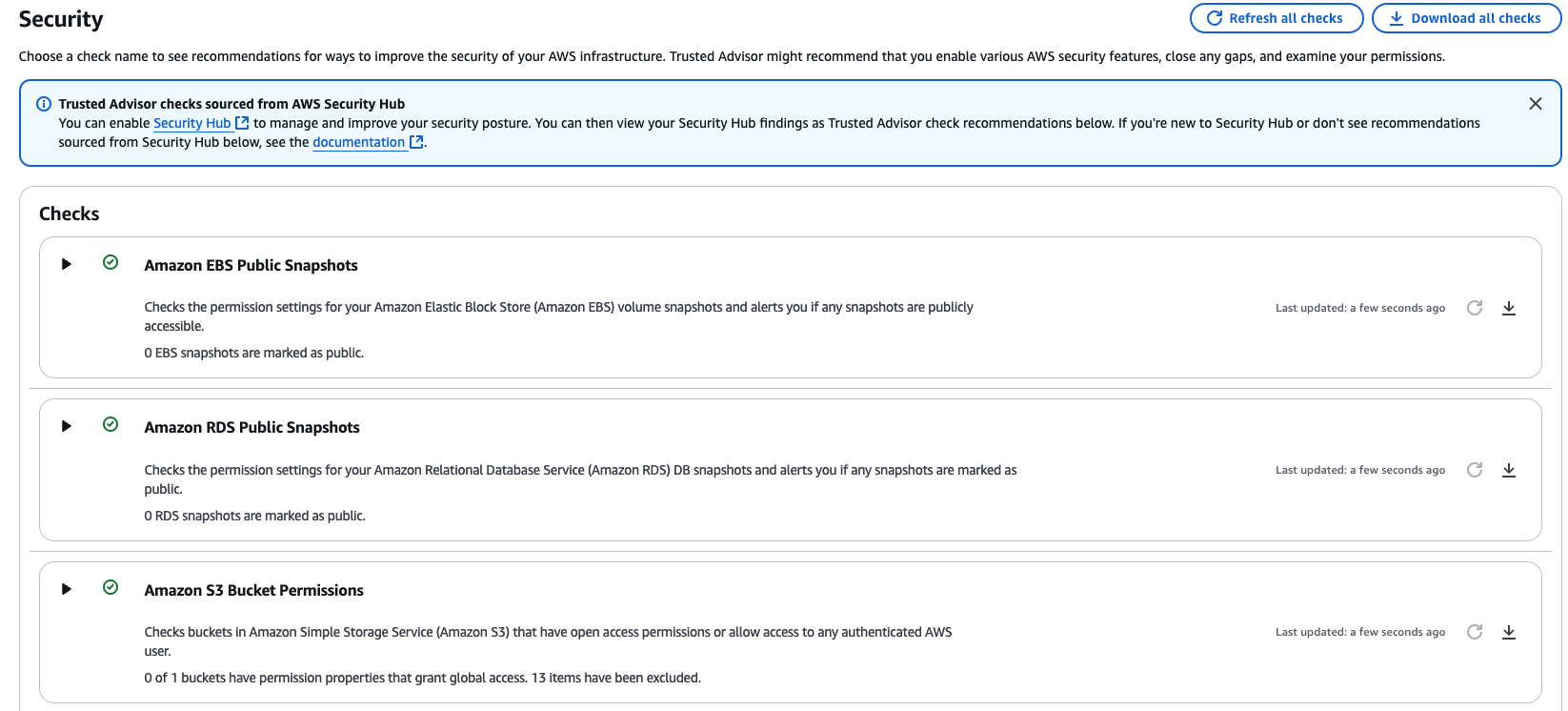
Trusted Advisor is a AWS Management & Governance Service that includes security capabilities as well. Trusted Advisor offers checks over 6 categories including security, performance, fault tolerance, service limits, operational excellence, and cost optimization.
One of these Trusted Advisor security checks that all AWS Accounts have access to is the Trusted Advisor check for Amazon S3 Bucket Permissions (Check ID: Pfx0RwqBli). This check looks for ACLs, bucket policies, and block public access status to evaluate S3 buckets for open access.
Relevant Trusted Advisor S3 Alert Criteria (from AWS):
- Yellow: A bucket policy allows any kind of open access.
- Yellow: Trusted Advisor does not have permission to check the policy, or the policy could not be evaluated for other reasons.
- Red: The bucket ACL allows upload and delete access for Everyone or Any Authenticated AWS User.
Technical Walkthrough
Note: We excluded 13 buckets from the Trusted Advisor check to also denote the difference between excluded and ignored buckets from AWS. Additionally, we used an account on the basic AWS Support plan, so we did not have access to the Trusted Advisor API.
With Block Public Access disabled at both the account and bucket level, the following could grant public access:
- Public Bucket Policy
The following S3 bucket policy will set public read via s3:GetObject on our target bucket.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PublicRead",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::fog-pub-acl/*"
}
]
}- Public Bucket ACLs
The following AWS CLI command will set public write and public write bucket ACLs.
aws s3api put-bucket-acl --bucket fog-pub-acl \
--grant-write uri=http://acs.amazonaws.com/groups/global/AllUsers \
--grant-read uri=http://acs.amazonaws.com/groups/global/AllUsersWith the above set, Trusted Advisor will report action recommended (red) as the bucket is now public. However, we can modify a bucket policy with one of the following payloads:
- A S3 Bucket Policy that denies
s3:GetBucketPolicyStatus - A S3 Bucket Policy that denies
s3:GetBucketPublicAccessBlock - A S3 Bucket Policy that denies
s3:GetBucketAcl
In this case, we’ll use s3:GetBucketPublicAccessBlock to craft a still public policy:
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "PublicRead",
"Effect": "Allow",
"Principal": "*",
"Action": "s3:GetObject",
"Resource": "arn:aws:s3:::fog-pub-acl/*"
},
{
"Sid": "DenyBucketBPA",
"Effect": "Deny",
"Principal": "*",
"Action": "s3:GetBucketPublicAccessBlock",
"Resource": "arn:aws:s3:::fog-pub-acl"
}
]
}When such a policy is applied, no high-severity or medium-severity Trusted Advisor alert is triggered. Upon refresh of the Trusted Advisor S3 Security Check, the check status reports as green (no problems detected).
Thus, we now have evaded detection by bypassing AWS Trusted Advisor’s S3 Security Check and configured a bucket with public and anonymous permissions via bucket policies and ACLs that permits for data access open to the world and potential data exfiltration - all without triggering a single alert.
Our Thoughts and Observations
Here’s our take on AWS’s response.
- It took 2 different fixes to fix what the findings we initially disclosed.
- The first fix was incomplete and only addressed changing the status of the finding to a warn. However, this did not address the inaccurate reporting on ACL status.
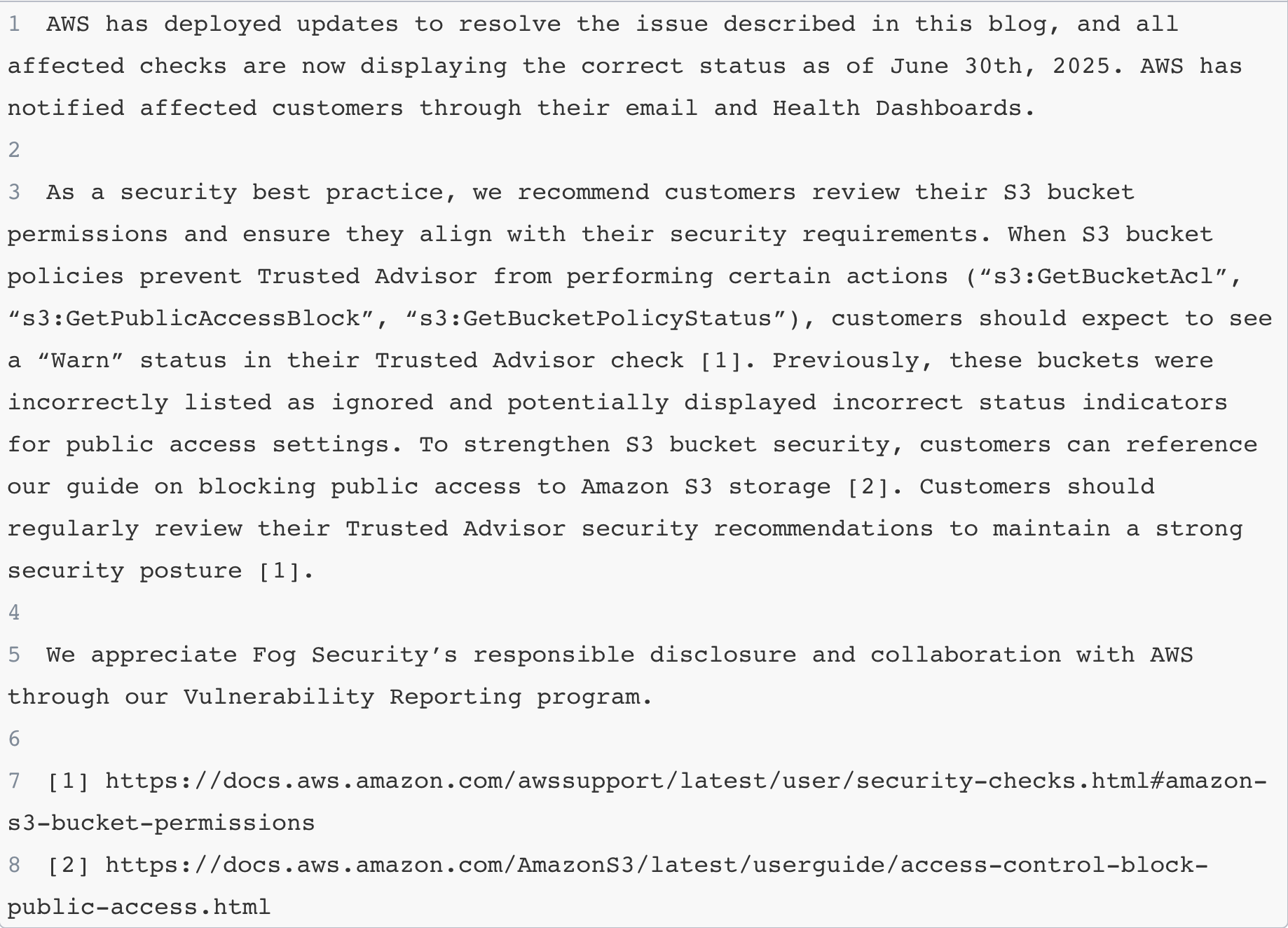
- Only after we retested and communicated the incomplete fix to AWS, the 2nd fix addressed the inaccurate ACL status reporting. AWS did not communicate to customers regarding the 2nd fix.
- We believe AWS’s communication downplays the severity of our findings.
- The email does not communicate that Trusted Advisor inaccurately reports public buckets. For clarity, we'd like to see explicit language on "potentially public buckets" as their communication does not include the word "public" and only indicates buckets.
- The email does not detail inaccurate results listed for ACLs and potentially missing “action recommended” (red) results. The email only mentions “WARN" and does not mention the missed "ERROR."
- AWS's communication states that the bucket is listed as "ignored" and that the "bucket is not considered". However, this is still factored in the Trusted Advisor check summary similar to a bucket that passed the check.
- The communication inaccurately states that the issue was resolved. The issue was resolved only after we retested and communicated the incomplete fix to AWS.
- Our testing account was not emailed by AWS. When we asked AWS about why we didn't receive notifications, they did not provide an answer. We believe their communication to be insufficient.
- While this is a technical detail, their email communication references an incorrect permission that would not work as a payload. Our findings include
s3:GetBucketPublicAccessBlockwhile their email referencess3:GetAccountPublicAccessBlock.s3:GetAccountPublicAccessBlockis not a supported action in S3 bucket policies and creating a bucket policy with that permission will fail with an error.
AWS Public Statement and Communications
Conclusion
While AWS provides multiple configuration options for enhancing S3 data security and access—such as ACLs, bucket policies, and Block Public Access Settings—our research highlights the complexity of how these settings interact. We found that certain combinations can evade security tooling and create publicly accessible S3 buckets without detection. Notably, detection by AWS’s own Trusted Advisor service could be bypassed with specific configurations.
We believe in customer transparency and that “security is job zero.” While we appreciate AWS addressing the issue, we believe the communication is lacking and downplays the impact of this issue. See Corey Quinn’s take on a recent security issue with Amazon Q and communication here.
AWS posted a public bulletin for a similar finding in 2023 here.
We recommend the following:
- Enabling AWS’s Block Public Access Settings at both the account and bucket level when possible.
- Checking S3 buckets and configuration to ensure data is secure and not unintentionally public. We have an open source tool, YES3 Scanner, that can scan for configuration issues: https://github.com/FogSecurity/yes3-scanner
- Retiring the usage of S3 ACLs if possible and use IAM policies instead.
- Reviewing buckets to see if your cloud data could have been impacted by these security issues.
If you have any questions or feedback on our research, contact us at info@fogsecurity.io.